The /etc/passwd file contains information about user accounts. It is world-readable, but usually only writable by the root user. Historically, the /etc/passwd file contained user password hashes, and some versions of Linux will still allow password hashes to be stored there. If we have write access to this file as a low level user, we can abuse this privilege to actually overwrite the root user’s password hash.
Method 1 – Overwriting root password
Do do this, let’s first check the file permissions on the /etc/passwd file. In our example, we can see that our user account has read/write access.ls -la /etc/passwd

Now we can use openssl to generate a new password hash in the format used by /etc/passwd.openssl passwd <newPassword>

Now let’s edit the /etc/passwd file and paste the newly generated hash between the first and second colon.vi /etc/passwd

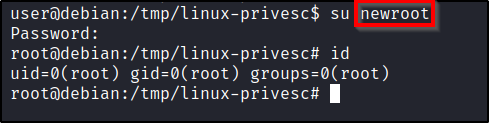
Finally, we can switch to the root user using the new password.su root

Method 2 – Creating a new user account
Alternatively, you could have also created a new user account with root group membership. This can easily be done in two steps:
- Copy the root user line, and paste it to the bottom of the /etc/shadow file.
- Place a password hash that you control between the first and 2nd colon.
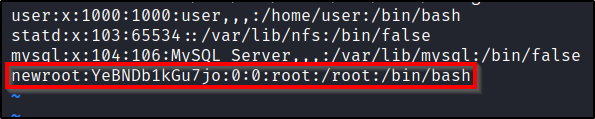
Once this is done, you can simply switch to the new user.su newroot