This post intends to serve as a guide for some of the most common HTTP Headers web applications use to prevent exploitation of potential vulnerabilities. Within this article, you will discover the name of the various headers, along with their use case and various configuration options.
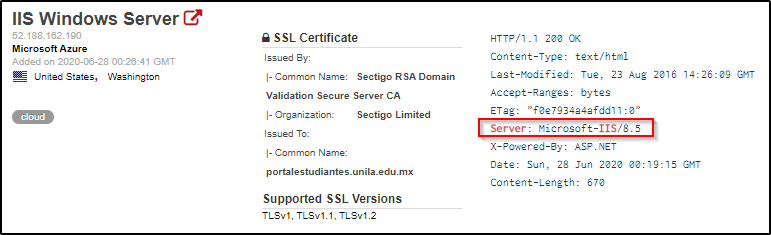
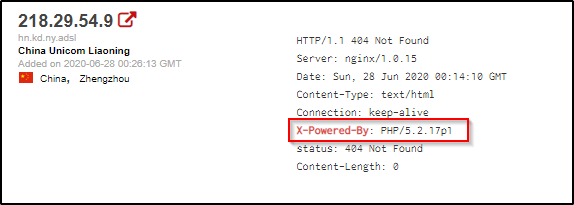
If you’d like to learn more about which headers may be leaking information about the software running on your webserver, check out my other post titled Have a WebApp? Here Are Three HTTP Headers Leaking Your Server Information.
Table of Contents:
- Strict-Transport-Security
- Content-Security-Policy
- Access-Control-Allow-Origin
- Set-Cookie
- X-Frame-Options
- X-XSS-Protection
- Additional Resources
STRICT-TRANSPORT-SECURITY
What does this header do?
HTTP Strict Transport Security instructs the browser to access the webserver over HTTPS only.
Why would we use this?
By enforcing the use of HTTPS, we’re ensuring that users accessing the web page has a secure, encrypted connection. This can also help users notice whether or not they are victim to man in the middle attacks if they receive certificate errors when a valid certificate is in place on the webpage.
What values can we set this header to?
There are 3 directives for this header:
Max-Age : Default value of 31536000. This is the maximum age (time) for which the header is valid. The server updates this time with every new response to prevent it from expiring.IncludeSubDomains : This applies control over subdomains of the website as well.Preload : This is a list that is maintained by Google. Websites on this list will automatically have HTTP enforced in the Google Chrome browser.
CONTENT-SECURITY-POLICY
What does this header do?
Content Security Policy is used to instruct the browser to load only the allowed content defined in the policy. This uses a whitelisting approach which tells the browser from where to load the images, scripts, CSS, applets, etc.
Why would we use this?
If implemented properly, we would be able to prevent exploitation of Cross-Site Scripting (XSS), Clickjacking, and HTML Injection attacks. We do this by carefully specifying where content can be loaded from, which hopefully isn’t a location that attackers have control of.
What values can we set this header to?
The values can be defined with the following directives:
default-srcscript-srcmedia-srcimg-src
EXAMPLE:
Content-Security-Policy: default-src 'self'; script-src runscript.com; media-src online123.com online321.com; img-src *;
This is would be interpreted by the browser as:
default-src 'self' : Load everything from the current domain.script-src runscript.com : Scripts can only be loaded from runscript.commedia-src online123.com online321.com : Media can only be loaded from online123.com and online321.com.img-src * : Images can be loaded from anywhere.
ACCESS-CONTROL-ALLOW-ORIGIN
What does this header do?
This header indicates whether the response can be shared with requesting code from the given origin.
Why would we use this?
This is used to take a whitelisting approach on which third parties are allowed to access a given resource. For example, if site ABC wants to access a resource on site XYZ (and is allowed to), XYZ will respond with a Access-Control-Allow-Origin header with the address of site ABC to instruct the browser that this is allowed.
What values can we set this header to?
The following directives can be used:
* : For requests without credentials, you can specify a wildcard to tell browsers to allow requesting code from any origin to access the resource.<origin> : Specifics a single origin.null : This should not be used.
SET-COOKIE
What does this header do?
This response header is used to send cookies from the server to the user agent, so the user agent can send them back to the server later. One important use of cookies is to track a user session, and can oftentimes contain sensitive information. Because of this, there are additional attributes that we can set for securing the cookies.
Why would we use the additional attributes?
Using these additional attributes can help protect the cookies against unauthorized access.
What values can we apply?
While there are many attributes for a cookie, the following are most important from a security perspective.
Secure : A cookie set with this attribute will only be sent over HTTPS and not over the clear-text HTTP protocol (which is susceptible to eavesdropping).HTTPOnly : The browser will not permit JavaScript code to access the contents of the cookies set with this attribute. This helps in mitigating session hijacking through
X-FRAME-OPTIONS
What does this header do?
This header can be used to indicate whether or not a browser should be allowed to render a page in a <frame>, <iframe> or <object>.
Why would we use this?
Use this to avoid clickjacking attacks. Without clickjacking protections, an adversary could trick a user to access a malicious website which will load the target application into an invisible iframe. When the user clicks on the malicious application (ex. a web-based game), the clicks will be ‘stolen’ and sent to the target application (Clickjacking). As a result, the user will click on the legitimate application without his consent, which could result in performing some unwanted actions (ex. delete an account, etc).
What values can we set this header to?
There are 3 directives we can use:
deny : This will not allow the page to be loaded in a frame on any website.same-origin : This will allow the page to be loaded in a frame only if the origin frame is same. allow-from uri : The frame can only be displayed in a frame on the specified domain/origin.
X-XSS-PROTECTION
What does this header do?
This header enables the Cross-site scripting (XSS) filter built into most recent web browsers.
Why would we use this?
The sole purpose is to protect against Cross-Site Scripting (XSS) attacks.
What values can we set this header to?
There are 3-modes that we can set this header to:
0; : Disables the XSS filter.1; : Enables the filter. If an attack is detected, the browser will sanitize the content of the page in order to block the script execution. 1; mode=block : Will prevent the rendering of the page if an XSS attack is detected.
Additional Resources
This is nowhere near an exhaustive list of the different security headers that you should be using. Should you like to learn more or dive into this topic deeper, I’d recommend checking out the following websites:
Essential HTTP Headers for Securing Your Web Server
Mozilla’s HTTP Headers Documentation